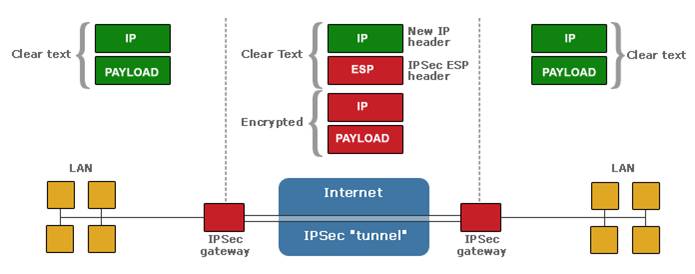
IES provides comprehensive solutions for Network Security, which encompasses distributed denial of service (DDoS) attack prevention, Universal Threat Management, Server protection, Endpoint protection, Email Protection, Application Monitor and Management, Encryption and so on.
We partner with globally renowned companies for Network Security hi-tech products, and this collaboration enables us to ensure foolproof security solutions to our customers.